Static Analysis
Dedaub's security suite offers an accurate and comprehensive EVM static analysis tool based on the state-of-the-art Dedaub decompiler.
Examples of static analysis warnings that can be identified by the Dedaub security suite:
- Accessible Selfdestruct
- Reentrancy / inconsistent reentrancy guards (read-only reentrancy)
- Call to Tainted Function
- DoS: various types
- Flashloan unchecked callback
- Permit omits sensitive variable
- Swap publicly reachable
- 50+ more warnings and growing
Additionally, contracts flagged by several kinds of static analyses are automatically fuzzed (i.e., analyzed dynamically) to see if funds can be lost.
Our static analysis is designed for scalable deployment over all smart contracts available. This allows us to identify contracts vulnerable to a novel attack vector in a timely manner. A subscription to the Dedaub security suite allows you to access this continuous static analysis of your contracts, as well as leverage continuous dynamic analysis.
One can access our static analysis in two distinct ways:
- Ecosystem-wide analysis (Enterprise users only) - This feature allows you to query our extensive warnings database to find contracts that fit a certain pattern or have a certain warning. This is useful for finding contracts that are vulnerable to a specific attack vector.
- Project-specific analysis (Individual users and up) - This feature allows you to upload your contracts and receive a detailed report on the warnings present in your contracts. This is useful for ensuring the security of your contracts before deployment.
Ecosystem-wide analysis
Further explanation on how to access such analysis can be found here: Ecosystem-wide Analysis. Do note this requires an Enterprise-level subscription.
Project-specific analysis
After uploading a project to our system via the Srcup tool, one can view a detailed report of the warnings present in the contracts via our triaging view. For example in this project there exists a reentrancy warning in the withdraw function of the SimpleProtocol contract. This allows you to quickly identify and fix the warnings present in your contracts.
Triaging view
This view is similar for both the ecosystem-wide and project-specific analysis. It allows you to view the warnings present in a contract and quickly triage them. This is useful for quickly identifying and fixing the warnings present in your contracts.
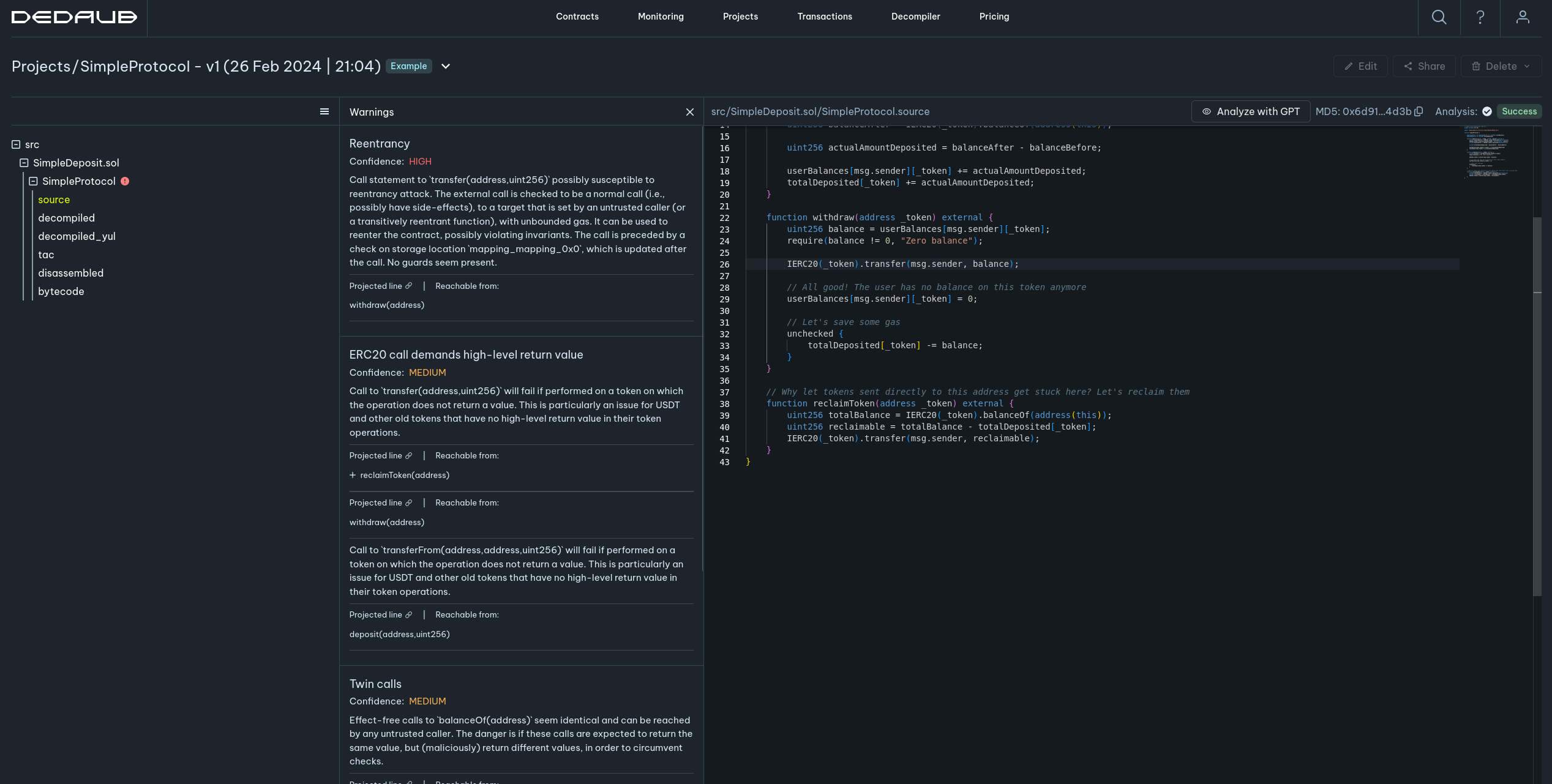
In the screenshot, the reentrancy warning corresponds to a critical vulnerability, where if an ERC777 token is used in this protocol an attacker could repeatedly call the withdraw function every time that the attacker gets called back, and drain the contract of its funds.
GPT Analysis for projects
Our system offers on-demand analysis of your project contracts using GPT technology. This analysis is complementary to our more traditional static analyses and could uncover issues or suggest improvements that we otherwise wouldn't. The findings are presented in a succint form, with inline code snippets to help with inspection:
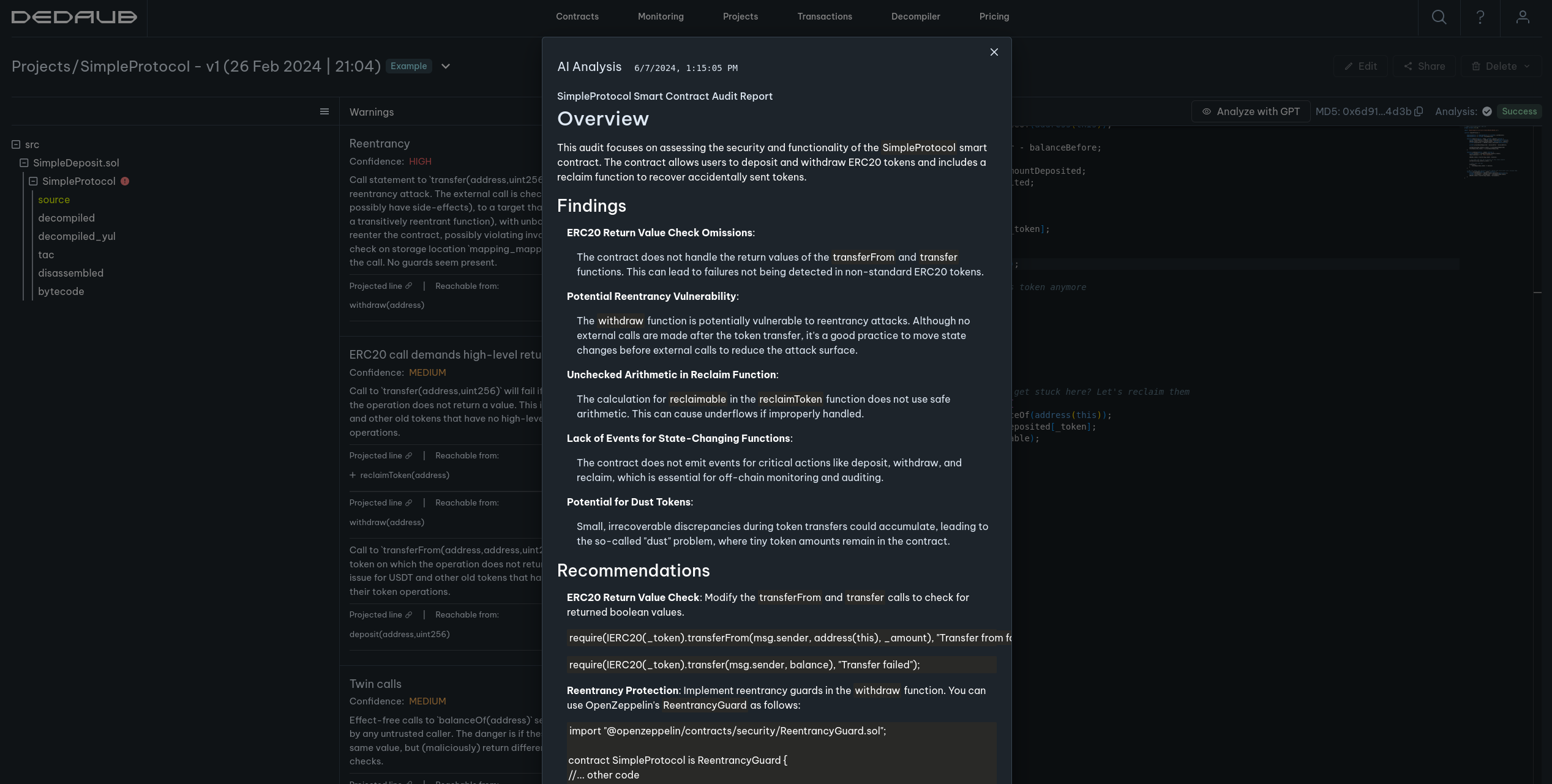
Interested?
If you are interested in using our comprehensive security suite on your project including real-time monitoring, continuous static/dynamic analysis and decompilation on all popular EVM chains such as Ethereum, Base, Optimism, Blast, Aribtrum, Avalanche and Polygon, please contact us using the form on https://dedaub.com.