Advanced Contracts Search
The "Contracts" functionality ("contract search", in full) is the first major piece of the Security Suite. It aims to be a proactive search for vulnerable, suspicious, or otherwise interesting code patterns, combined with queries over the state of accounts.
Contract search combines filters based on static analyses, current contract state (including balances, allowances, deployment/last transaction time), human inspections, code strings, and more. Additionally, contracts are organized into protocols, so queries can be narrowed down to a specific protocol of interest.
The Contracts Page
Navigate to the contracts page by clicking on the 'Contracts' nav item. You can then select the appropriate network from the network dropdown on the top left of the screen.
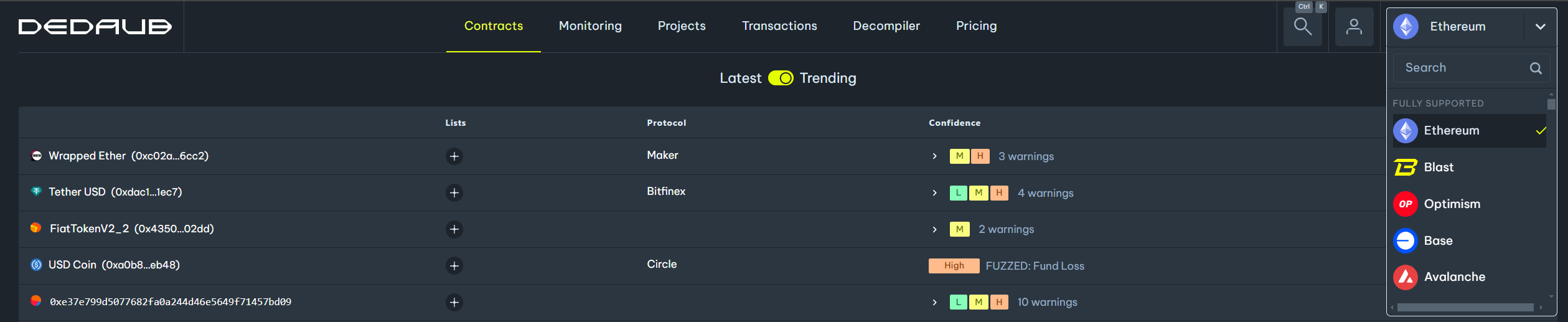
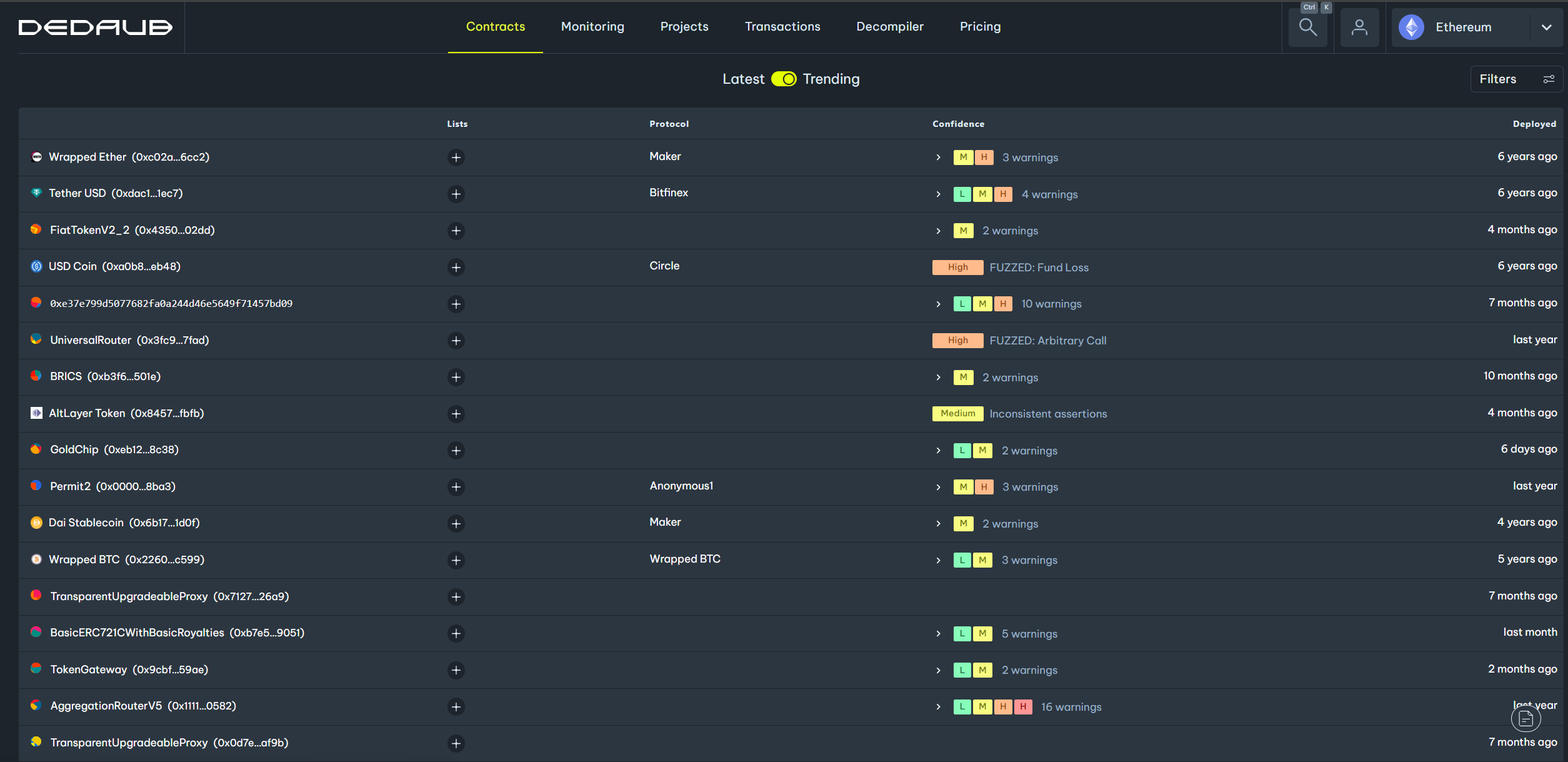
The table below displays the name (or address, if the name is unavailable) of each contract, the associated protocol, the types of warnings detected on the contract, the confidence level of our system in the validity of each warning, and the date on which the contract was deployed.
 )
)
Contract Filters
To narrow down the list of contracts, you can apply filters. Click on the 'Filter' button on the top right to open the filters drawer. Then, select the filters you are interested in and click 'Apply'.
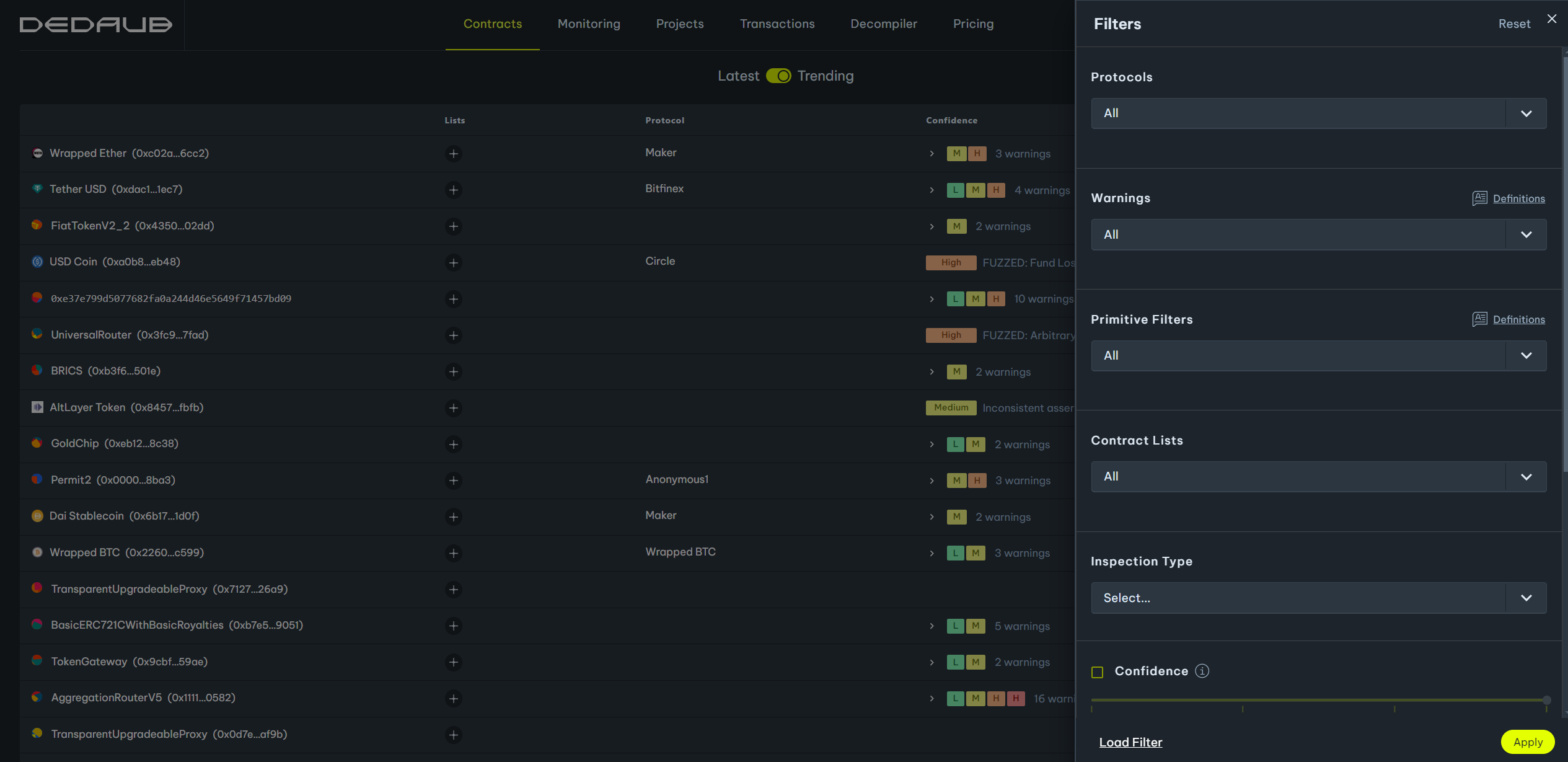
Warnings
Our static analysis tools recognize and flag many tens of potential bugs or bad smells in Solidity code. To limit your search to contracts that have been flagged as having a vulnerability of a specific type, select from the warning type dropdown list. Hover over each option for a more detailed description of each warning type. You can select multiple warning types. You may learn more about our static analysis in the dedaub analysis documentation.
Primitive Filters
The primitive filters enable filtering based on a contract's state, rather than its code. They can be used to filter contracts based on their balance, deployment date, transaction activity, and more. Hover over each option in the dropdown list for a more detailed description of what each primitive filter does. Multiple primitive filters can be selected.
Contract Lists
You can save contracts in lists (we will cover this in a later tutorial). To search for contracts within one of your defined lists, select that list in the filter drawer. You can expand your search by selecting more than one list.
Inspection Type
Some of the warnings generated by our static analysis tools are inspected by our team of auditors. You can filter contracts based on whether their warnings have been inspected. The inspection determines whether the warning is a "True Positive" (unsafe contract) or a "False Positive" (safe contract).
Confidence
Our static analysis tool assigns a confidence level to every warning it flags. This level can be used to focus code inspections on areas where there is a higher chance of the warning being a true positive. Higher confidence means that the warning is more likely to be valid with all else being equal. However, all else is typically not equal! If you focus on high-confidence warnings for contracts that hold significant funds, for instance, you are unlikely to find valid warnings. (If it were that easy, others would have noticed the bug.) Instead, lower-confidence warnings may indicate something suspicious that ends up being a valid vulnerability--for instance, if the problem superficially appears to be prevented by some check, but is not really prevented.
The standard advice is:
- If a contract is of value (to you, or to all), inspect warnings at level "MEDIUM" and above. This is the case if you are a protocol owner or auditor and you limit your search to a few tens of contracts that you want to inspect thoroughly.
- If you are doing a search for interesting issues over a large set of contracts:
- set the minimum confidence to "HIGH"; OR
- set the minimum confidence to "MEDIUM" and combine with a strict primitive filter, such as "Large Value". (If the value should be in allowances and not in balances, also add "Balance and Allowance".)
Basically, "MEDIUM" means "the analysis sees evidence that this is most likely a false positive (otherwise it would have been a "HIGH" or "HIGHEST") but might be worth a look".
Full text search on source
You can use the search function to locate contracts that contain specific text in their code. This feature enables you to search for contracts with particular functions, events, errors, or variables defined within them, providing a more efficient way to locate relevant contracts.
Full text search on decompiled
Queries on decompiled code are valuable when there is no source code available, but also when multiple source code patterns normalize to the same intermediate code--e.g., after comments and blanks are removed, or when variable names are normalized.